In the last weeks, new guests in our Azure Active Directory / Office365 received the message “Your sign-in was blocked” – “We’ve detected something unusual about this sign-in.“
For standard users, you can just fix this by remediating the risky sign-in of the user in: Azure Active Directory – Security – Risky users (https://portal.azure.com/#blade/Microsoft_AAD_IAM/SecurityMenuBlade/RiskyUsers). But this does not work for guests!
The issue is: The Identity Protection risk-based policies (User risk policy, Sign-in risk policy and MFA registration policy) are usually configured for all users (which is good) and therefore also for guests. Even if the guests have MFA activated, there is a good chance that especially the User risk policy is triggered. If that happens for a guest user, you don’t see it in risky sign-ins overview, because the guest is not in your Active Directory – so it’s nothing you can control. The official Microsoft explanation is:
- If a guest user triggers the Identity Protection user risk policy to force password reset, they will be blocked. This block is due to the inability to reset passwords in the resource directory.
- Guest users do not appear in the risky users report. This loss of visibility is due to the risk evaluation occurring in the B2B user’s home directory.
- Administrators cannot dismiss or remediate a risky B2B collaboration user in their resource directory. This loss of functionality is due to administrators in the resource directory not having access to the B2B user’s home directory.
Solution
There are two solutions available:
Option 1 – Create a dynamic group with all guests which is excluded from user risk policy:
- Create a new dynamic group in Azure Active Directory:
- Group Type: Security
- Group name: Guests (or whatever you want)
- Membership type: Dynamic User
- Add dynamic query:
- userType Equals Guest
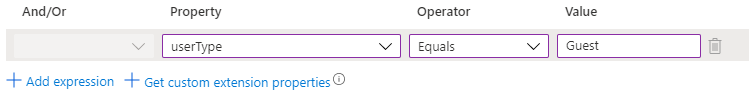
- Save the group and wait a few minutes till you see the guest users in All members.
- Open User risk policy under: Azure Active Directory – Security – User risk policy (https://portal.azure.com/#blade/Microsoft_AAD_IAM/IdentityProtectionMenuBlade/UserPolicy)
- Exclude Guests from the policy
Option 2 – Tell the guest that their administrator has to remediate the risk
- Instruct the guest that their IT should go to:
https://portal.azure.com/#blade/Microsoft_AAD_IAM/SecurityMenuBlade/RiskyUsers - If the user is not listed – click “Load more”
- Dismiss the risk for the user
Further information
- Identity Protection and B2B users: https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/concept-identity-protection-b2b



No responses yet